OpenID Authentication
Kasm can utilize external authentication providers using OAuth, including OpenID Connect (OIDC) providers.
Be mindful when configuring OpenID providers that are public. Any user that can successfully authenticate with the provider will have access to your deployment of Kasm Workspaces. While access to Kasm Workspace apps and desktops can be resitricted with Kasm group permissions, any user of the public authentication provider would still be able to login to your deployment of Kasm. It is recommended to use a private OpenID provider unless your intention is to allow authentictioned access to all users of the OpenID platform provider.
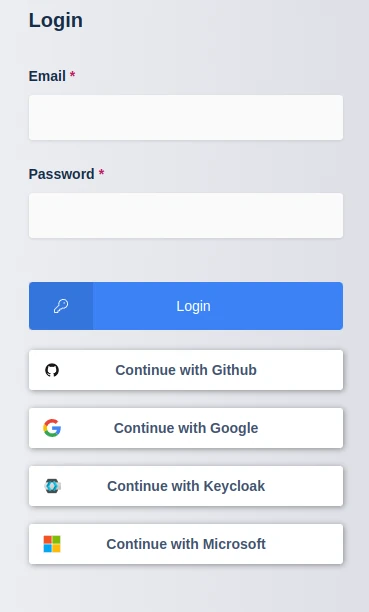
Configuration
OpenID configuration can be found under the Access Management -> Authentication tab in the Admin Navigation Bar.
| Property | Description |
|---|---|
| Enabled | When checked this configuration will be active. |
| Display Name | This name is displayed on the login page to represent the authentication provider. (e.g Continue with Github) |
| Logo URL | A URL to a login logo image for the authentication provider. (e.g https://github.com/favicon.ico) |
| Auto Login | When checked, the user will be automatically navigated to the OIDC provider when they view the login screen. This only applies if a single authentication provider is visible. If this configuration is set, the fixed login page (without redirection) can be accessed via /#/staticlogin |
| Hostname | The URL hostname (e.g kasm.example.com) of the deployment. This OIDC config will only be displayed when the deployment is accessed via this URL host name. This allows for a single deployment to service multiple tenants who may need different OIDC configurations. If Default is defined, this config will apply regardless of the host name. |
| Default | If checked this OIDC config will be shown on the login screen of the deployment when access with any hostname, unless another config is defined with the specific hostname. |
| Client ID | The Client ID received from the authentication provider. |
| Client Secret | The Client Secret received from the authentication provider. |
| Authorization URL | The authorization url for the authentication provider. (e.g https://github.com/login/oauth/authorize) |
| Token URL | The token url for the authentication provider. (e.g https://github.com/login/oauth/access_token) |
| User Info URL | The user info url for the authentication provider. (e.g https://api.github.com/user). This service will be queried if the Username Attribute or Groups Attribute are not provided by the identity provider in the id or access tokens. |
| Scope | The OIDC Scopes for the authentication provider. Enter one scope per line. e.g: openid email |
| Username Attribute | The attribute from the authentication provider to use for the username within Kasm (e.g email). The system will search the access_token, id_token and user_info api for this property. |
| Groups Attribute | The attribute from the authentication provider to user for group membership mapping within Kasm (e.g groups). The system will search the access_token, id_token and user_info api for this property. This field is optional, but if defined, authentication will fail if the group attribute is not found. |
| Debug | When checked, the OIDC access and id tokens are logged as well as the response from the user_info api if queried. TLS Verification is disabled for the Authorization URL, Token URL, and URL Info URL API interactions. This feature should remain disabled unless needed for troubleshooting. |
| Redirect URL | The identify provider can be configured to allow access to redirect to this URL. https://<deployment hostname>/api/oidc_callback |
| OpenID Connect Issuer | An OIDC provider has an issuer value. This is a complete URL, e.g: https://oidc.host/realms/master |
| Logout with OIDC Provider | If checked, the user will be redirected to the OIDC provider's logout page after logging out of their Kasm session. Requires OpenID Connect Issuer to be configured. |
| Enable OIDC SLO Frontchannel Endpoint | If checked, Kasm will honor frontchannel logout requests from the OIDC provider. If available, also configure OpenID Connect Issuer for verification. Note: where possible, backchannel logout is recommended over frontchannel as it is more stable and secure. |
A non redirecting login page is at https://hostname/#/staticlogin when auto login is enabled.
Group Assignment
Users that auth via OIDC, can automatically be associated with Groups defined in Kasm. To automatically assign groups:
- In the OpenID Authentication configuration, ensure the Groups Attribute is defined to match the corresponding group attribute of the IDP.
- Navigate to the Access Management -> Groups tab in the admin navigation bar.
- Using the arrow menu select Edit of the desired group.
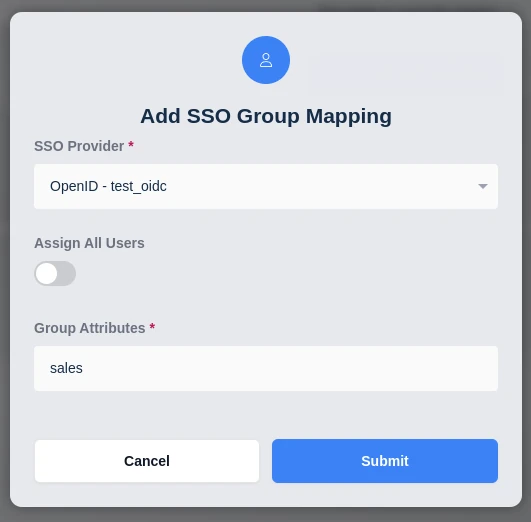
- Navigate to the SSO Group Mappings tab and select Add SSO Mapping.
- Select the OpenID IDP for example "OpenID - test_oidc" for the SSO Provider.
- Enter the group name used in the identity provider for the OpenID Group Name field, either preceded by a forward slash (e.g.
/sales) if the OIDC Provider has Full Group Path set to On, or without a preceding forward slash (e.g.sales) if Full Group Path is set to Off.
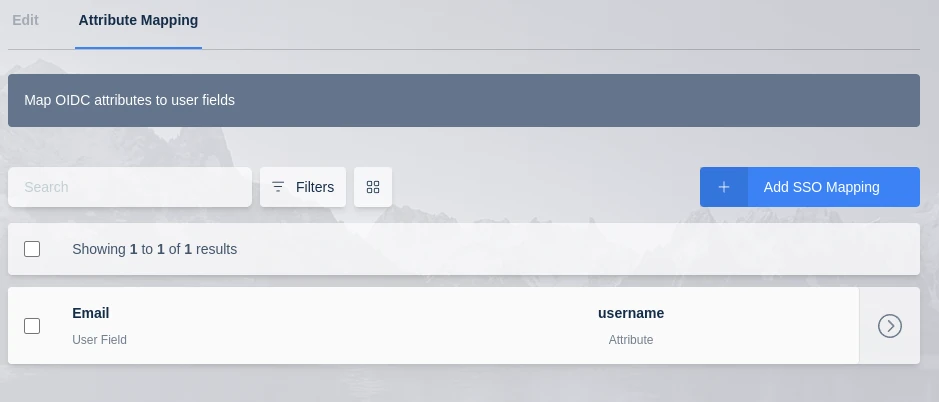
OpenID Attribute Mapping
Additional OpenID attributes can be passed with the login redirect. Administrators can optionally map those attribute values to fields on the Kasm user. See the documentation for your OpenID provider for a listing of attributes.
These can be configured by editing an existing OpenID Authentication configuration, if creating a new configuration you will need to submit and edit to add them.
The following Kasm User fields can be populated with values from OpenID attributes.
- First Name
- Last Name
- Phone
- Organization
- Notes
- City
- State
- Country
- Custom Attribute 1
- Custom Attribute 2
- Custom Attribute 3
Kasm can log all OpenID attributes present in the login event, this is helpful for determining the attribute names. Add an OpenID Attribute Mapping with an attribute name of 'debug' and target any user field. The next time a user logs in, all OpenID attributes and values will be logged by Kasm.
Single Logout
Kasm supports the Single Logout (SLO) mechanisms defined by the OpenID Connect protocol.
- Backchannel (server-to-server) SLO is enabled as long as the
OpenID Connect Issuervalue is configured - Enabling
Logout with OIDC Providerwill direct the user's browser to the OIDC provider's logout page once they have logged out of Kasm - Frontchannel (iframe-in-browser) logout requests are not honored unless
Enable OIDC SLO Frontchannel Endpointis checked
Please see the example configurations for more information on SLO.