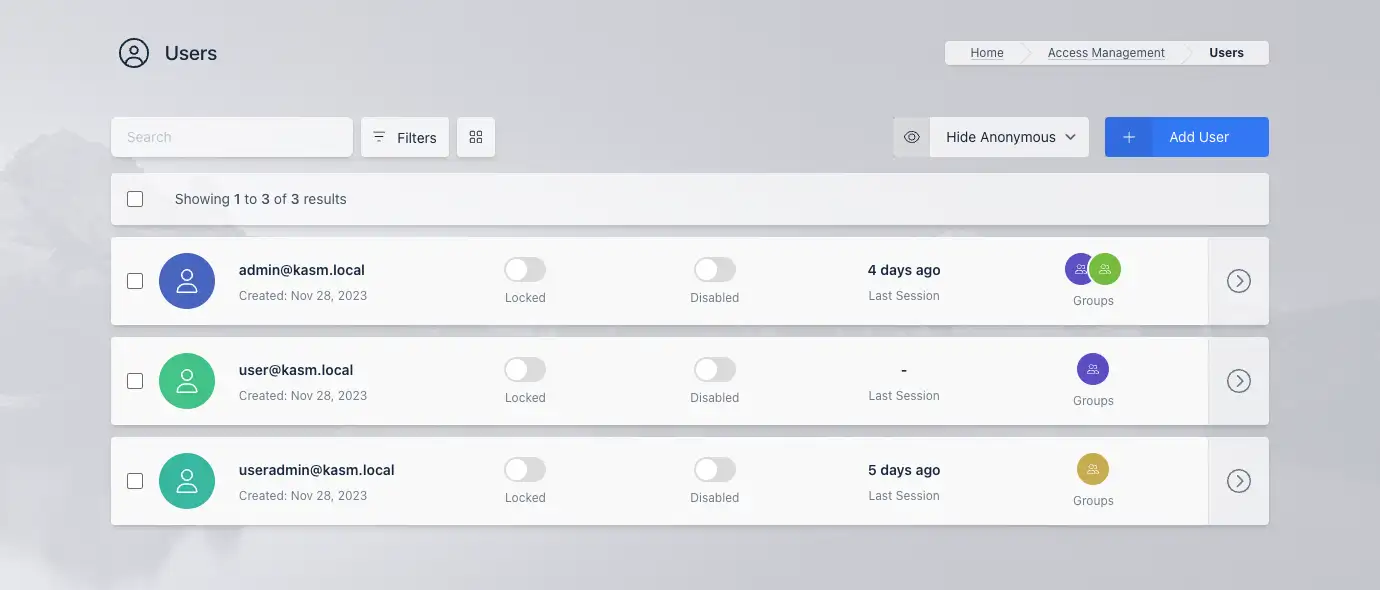
Users
Users must first be added to the server and then added to a group to manage their permissions. User permissions can be set by updating the group settings found here..
By default Anonymous users are hidden, if you wish to see them, click on the dropdown next to Add User and pick between, Hide Anonymous, Show Anonymous and Only Anonymous.
Create User
- Select Access Management > Users from the navigation menu.
- Select Add User from the top right of the Users table.
- Fill out Users information with User properties below.
User Properties
| Name | Description |
|---|---|
| User Name | Username for login |
| Password | Password for login |
| First Name | User's first name |
| Last Name | User's last name |
| Realm | SSO that the user belongs to (local, LDAP, SAML, OIDC) |
| Notes | Notes about user |
| Locked | Lock account |
| Disabled | The account is disabled. The user cannot login or authenticate until re-enabled by an administrator. |
| Reset Two Factor Authentication Secret | Reset the 2FA secret. The users will be required to re-initialize the 2FA upon next login. |
| Force Password Reset on Login | Force the user to change their password on the next login. This setting applies only to local accounts. |
| Organization | Organization Name |
| Last Session | Last login time |
| Phone | Phone number |
| City | City |
| State | State |
| Country | Country |
| Email address | |
| Custom Attribute 1 | Attribute to be used for custom purposes. |
| Custom Attribute 2 | Attribute to be used for custom purposes. |
| Custom Attribute 3 | Attribute to be used for custom purposes. |
| Encryption Key | An encryption key optionally used in Storage Mappings to encrypt and obfuscate files at rest. A key is automatically generated for each user but can be replaced if desired. See Custom Storage Provider Setup |
| Encryption Salt | An encryption salt optionally used in Storage Mappings to encrypt and obfuscate files at rest. A key is automatically generated for each user but can be replaced if desired. See Custom Storage Provider Setup |
Add User to Group
- Select Access Management > Groups from navigational menu.
- Select Edit from the arrow menu of the group you want to add the user.
- Select the Users Tab.
- Select Add User from Users in Groups table.
- Select the user you wish to add from dropdown menu and click Submit.
User Settings
Users have the ability to change settings by visiting their profile.
-
Auto Launch Session.
Automatically launch a session when the user logs in. Kasm Workspaces will use the configured Default Workspace Image.
-
Chat Sound Effects.
Enable Sound effects for chats during shared sessions.
-
Default Workspace Image.
The Default Kasm Image to use. This is the Image that is used for the /go URL, clicking the Launch Now menu item, and for Auto Launch Session. This item overrides the corresponding group setting if defined.
-
Show Tips During Session.
By default the user is shown a Tip that describes how to find and use the control panel. This tip can be suppressed by setting this item to false.
-
Toggle Control Panel.
Open and close the control panel within a Kasm session by pressing the Ctrl key twice.
-
Theme.
Select the Kasm Workspaces app theme, there is also an auto setting that will use the OS setting of the user's local computer.
User Permissions
The users permissions tab gives a breakdown of the resultant permissions a user has based on the groups they are a part of. If you want to give specific permissions you will need to create a group with those permissions and add the user to that group.
In order to change the permissions:
- Select Access Management > Groups from navigational menu.
- Select Edit from the arrow menu of the group you want to modify the permissions of (or create a group).
- Select the Permissions Tab.
- Click the Add Permissions button.
A full list of the options available is here.
User File Mappings
File Mappings allow the administrator to manage files to be mapped to the inside of a user's container based Workspace session. File Mappings can be defined on a User, Group, and/or Workspace. See the primary documentation on File mappings for more details.
User defined File Mappings can only be defined by the administrator.
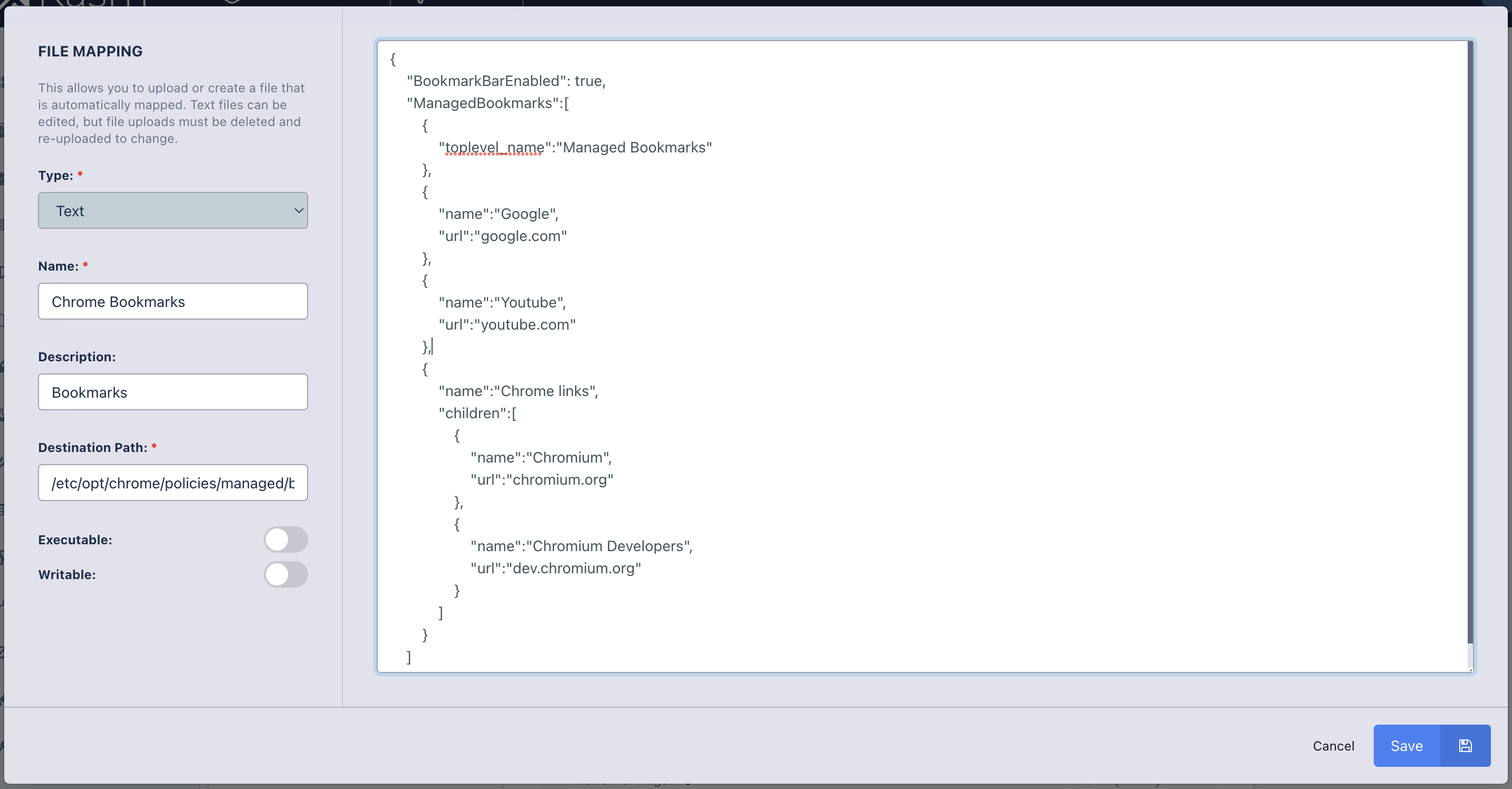
The following is an example File Mapping of a Chrome Managed Policy to define bookmarks in Chrome.
Bulk Import
Users can be created in bulk through the "Import Users" button on the User administration page.
The ensuing import wizard will expect a utf-8 encoded CSV file, with a size limit of 10,000 records.
Bulk import is an all-or-nothing operation; if any errors are found, none of the CSV data is imported into Kasm.
If there are errors in the file, the interface will present an interactive table that displays the errors alongside the CSV data. The field(s) for each error are enclosed in parentheses ( ).
Click the information button for a row to inspect the errors:
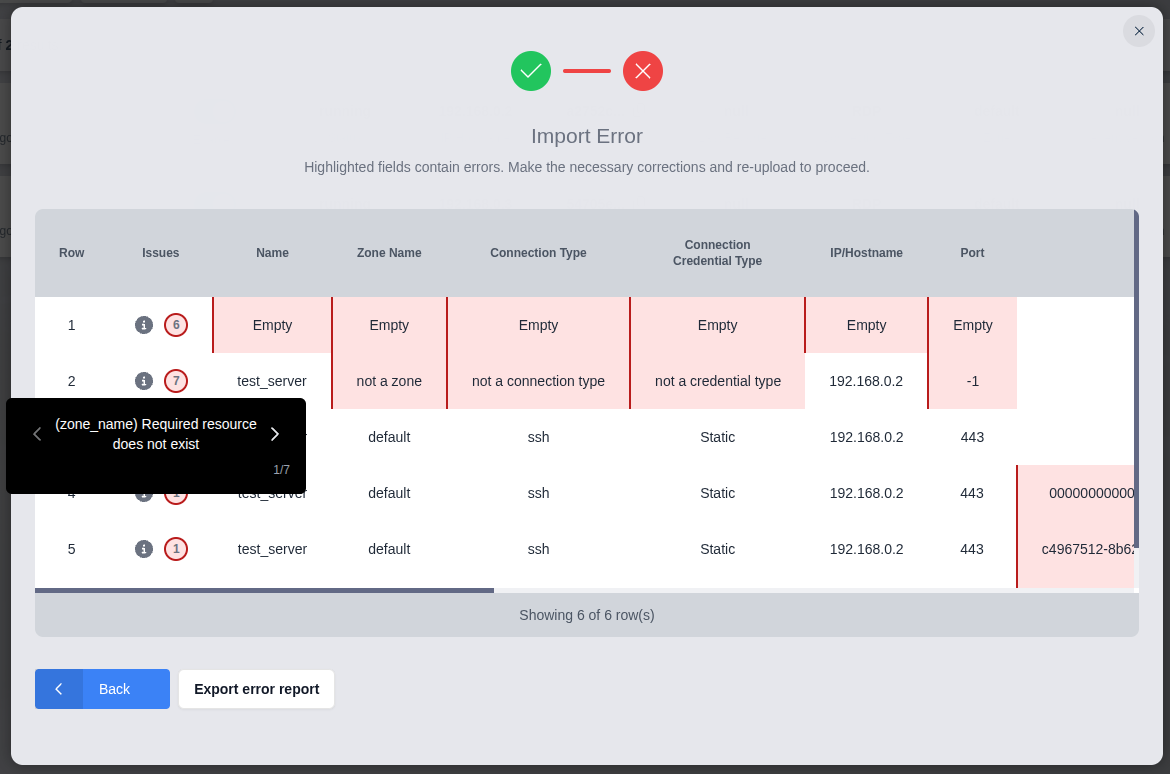
The import wizard provides the option to download the marked-up data for further inspection. This format adds an "issues" column to the beginning of the data that lists all of the errors for each row. In addition to the localized error messages shown in the import wizard, this data also includes the untranslated error message from the Kasm server for each field. The untranslated message is enclosed by square brackets [ ].
Below is an abridged sample from the exported CSV error report produced by clicking "Export error report" in the image above:
issues,name,zone_name,connection_type,connection_credential_type,ip_hostname,port,pool_id,assigned_username,windows_service_installed,connection_username,connection_password,sso_username_domain,passphrase,private_key,use_user_private_key,connection_info,max_simultaneous_sessions,max_simultaneous_users,labels
"(name) Wrong data type [Input should be a valid string]; (zone_name) Wrong data type [Input should be a valid string]; (connection_type) Bad value for enum [Input should be 'KasmVNC', 'RDP', 'VNC' or 'SSH']; (connection_credential_type) Bad value for enum [Input should be 'STATIC', 'SSO_CREATE_USER', 'SSO_USERNAME', 'SMARTCARD' or 'PROMPT_USER']; (ip_hostname) Wrong data type [Input should be a valid string]; (port) Wrong data type [Input should be a valid integer]",,,,,,,,,,,,,,,,,,,
"(zone_name) Required resource does not exist [Zone(not a zone) does not exist]; (connection_type) Bad value for enum [Input should be 'KasmVNC', 'RDP', 'VNC' or 'SSH']; (connection_credential_type) Bad value for enum [Input should be 'STATIC', 'SSO_CREATE_USER', 'SSO_USERNAME', 'SMARTCARD' or 'PROMPT_USER']; (port) Value is too small [Input should be greater than or equal to 0]; (connection_info) Invalid JSON [Value is not a valid JSON string]; (max_simultaneous_sessions) Value is too small [Input should be greater than or equal to 1]; (max_simultaneous_users) Value is too small [Input should be greater than or equal to 1]",test_server,not a zone,not a connection type,not a credential type,192.168.0.2,-1,,,,,,,,,,{test,0,0,
"(assigned_username, pool_id) Invalid combination [User assignment requires a Server Pool]",test_server,default,ssh,Static,192.168.0.2,443,,user@kasm.local,,,,,,,,,,,
The Developer API also exposes the /api/public/batch_create_user endpoint for programmatic use.
CSV Formatting
Kasm Workspaces requires that imported CSV files to adhere to the following format specifications.
- The file must be
utf-8encoded. - Fields are comma-separated (
,). Commas and linebreaks inside of a double-quoted field value will be interpreted as part of the value and not as a new field or line marker. Example:a,"b,c",dwould separate into three fields,a,b,c, andd. - A header row is required.
- Empty fields, which includes those whose content is a quoted empty string (
""), will be interpreted asnull. - Double-quote characters inside of a field can be escaped with duplication. Example:
"12""34"in a CSV field would produce12"34. - All rows must have the same number of columns.
User CSV Schema
The CSV file for User bulk imports recognizes the following columns. Optional columns may be omitted if they are not needed for any record. The descriptions from the "User Properties" section above apply to these fields, except where noted.
| Column Header | Required | Default | User Property | Notes |
|---|---|---|---|---|
| username | Yes | User Name | ||
| password | No | See note | Password | If omitted or null, the server will generate a random default password for the User. Warning Whitespace will be honored for this value. |
| realm | No | "local" | Realm | |
| sso_config_id | Conditionally | null | This is the ID (UUID) of the SSO configuration in the Kasm database. Required for OIDC and SAML realms. | |
| first_name | No | null | First Name | |
| last_name | No | null | Last Name | |
| notes | No | null | Notes | |
| lock_account | No | false | Locked | |
| disable_account | No | false | Disabled | |
| force_password_reset | No | false | Force Password Reset on Login | |
| organization | No | null | Organization | |
| phone_number | No | null | Phone | |
| city | No | null | City | |
| state | No | null | State | |
| country | No | null | Country | |
| No | null | |||
| custom_attribute_1 | No | null | Custom Attribute 1 | |
| custom_attribute_2 | No | null | Custom Attribute 2 | |
| custom_attribute_3 | No | null | Custom Attribute 3 | |
| encryption_key | No | null | Encryption Key | Warning Whitespace will be honored for this value. |
| encryption_salt | No | null | Encryption Salt | Warning Whitespace will be honored for this value. |
| group_... | No | null | The file may contain any number of "group_*" columns, e.g. "group_1", "group_2", etc. Each should contain the name of an existing Kasm User Group that the user will join. Groups that all users join by default, such as the "All Users" system group, do not need to be listed. |
Below is an example of a valid User CSV file. It contains all columns, including several groups. It would generate three users:
- A local user. Their password is automatically generated, but required to be changed upon login. They are a member of 3 additional specified groups.
- A user that exists in an OIDC SSO solution. They are a member of 1 additional specified group.
- A user that exists in the LDAP system configured for use with the Kasm deployment. They are a member of no additional groups.
username,realm,password,sso_config_id,email,last_name,first_name,organization,phone_number,city,state,country,encryption_key,encryption_salt,lock_account,disable_account,force_password_reset,notes,custom_attribute_1,custom_attribute_2,custom_attribute_3,group_1,group_2,group_3
jane.smith@ourorg.local,local,,,localuser1@ourorg.local,Smith,Jane,Our Organization,+12345678900,London,,UK,,,false,false,true,,,,,Other Admin Group,Finance,Data Managers
alice@ourorg,oidc,,00001111-2222-3333-4444-555566667777,alice@ourorg.local,,Alice,,,,,,,,,,,,,,,Other Admin Group,,
bob,ldap,,88889999aaaabbbbccccddddeeeeffff,,,,,,,,,,,,,,,,,,,,